CUSTOM IT SOLUTIONS THAT SIMPLIFY YOUR BUSINESS.
CCS delivers an entire suite of IT services to meet your budgetary and project goals. Our services can be utilized for any industry and are always delivered on schedule.
Our IT Services
CCS employs experienced and certified engineers who understand your needs. We build relationships with our partners which allows us to deliver cost-effective and high tech solutions directly to our clients. We utilize the newest technology wherever possible and treat our customers’ time as if it were our own.
IT Audits
Hardware Procurement
Relocation & Cabling
Desktop Design and Deployment
Phishing Test & Security Awareness
As phishing attacks become more common, it’s important to make sure your users are safe. CCS offers phishing training and simulations, to make sure your network and users are secure.
Network Design and Architecture
Wireless Solutions
Virtualization
With virtualization, you can launch a new server, increase memory or processing power, and expand storage in minutes, as opposed to hours. Virtualization also makes disaster recovery more possible, offering you peace of mind and greater flexibility in the event of a server crash or data center loss.
Vulnerability Scanning
With digital threats looming around every click, CCS understands how important network security is to your business. We stay one step ahead so attackers don’t ever get the chance to exploit vulnerabilities.
IT Audits
IT Audits can help identify problems before they become reality. With the numerous amount of new SEC and HIPAA laws and regulations, you can stay ahead of the curve and ensure your business is working within the safeguards of the law and in compliance with all standards of your industry.
By definition, An information technology audit, or information systems audit, is an examination of the management controls within an Information technology (IT) infrastructure. During an IT Audit, CCS will evaluate all areas of your business and it’s relation to technology.
In addition, if you are unaware of what you currently have running in your environment, what your users and employees have installed on their workstations, or are between IT firms, an audit is the place to start in identifying these issues.
CCS will provide a detailed report on the following areas:
IT Security
- What security measures are in place
- Passwords policies, Antivirus, Web Filtering, Firewall
- Where can security be improved
- Where are the current risks that need immediate addressing
Systems and Architecture
- Server inventory
- Assess the stability and performance of all servers
- Workstation inventory
- Networking Device inventory
- Security assessment on all networking devices
- Attempt brute force and hacking routines on the network to identify flaws
- and possible breach points
- Assess all online and cloud based services
Application Inventory
- Understand what applications are installed and running on your network
- Document warranty and license information for all business software
- Recommend tools to prevent the unauthorized installation of rogue software into your network
View our fact sheet and sample audit reports such as:
Hardware Procurement
Over the years, CCS has built strategic partnerships with a range of IT companies enabling us to offer the products that are right for your business. The procurement of hardware does not have to be a difficult task.
The Process
- A CCS engineer will analyze your current hardware infrastructure
- Recommendations will be made keeping future growth and budget in mind
- CCS will see the entire process through from ordering equipment, delivery tracking, and scheduling installation.
Some of our strategic IT partners








Relocations and Cabling
Moving your Business and need IT assistance? CCS engineers can help plan a move and ensure your IT infrastructure is up and running with minimized downtime.
Relocations
If you are moving your business, CCS has the experience and bandwidth to facilitate a smooth transition of your IT infrastructure. Analyzing and determining risks and needs will allow us to put together a plan that will minimize downtime and ensure a successful move of your business.
Cabling
CCS uses experienced and licensed electricians for all electrical and low voltage wiring.
New office installations
Co-ax and CAT 5/6 cable moves
Existing in-wall cable upgrades (Maximize the data throughput in your office network)
Telephone and VOIP cabling
Server closet re-organization
Desktop Design and Deployment
CCS employs Microsoft Certified engineers utilizing the latest in desktop imaging tools, technology, and practices.
Deploying workstations, applications, settings, and custom configurations manually, is a time consuming and costly venture. Here is how CCS can streamline your desktop deployment process:
Desktop Images
- By creating a master image of one workstation or desktop, we can essentially “mirror” that image on top of all your workstations. This saves hours of deployment costs and guarantees that each of your workstations will be setup with the same operating system, applications, settings, and user customizations.
- For larger organizations, utilizing Microsoft SCCM (System Center…..) images can be deployed over the network streamlining the process even further. A review of your organization will allow us to best determine the fastest and most efficient method of image deployment for your organization.
Group Policy
- Utilizing Microsoft Windows Server Group Policy Management, settings and corporate policies and be “pushed” out to all computers that are part of your network’s domain. This avoids the hassle of interrupting workflow, losing valuable time going from machine to machine, and human error.
- Scenario 1 –
Issue: A new application requires specific firewall rules to be in effect
Resolution: A group policy with the new rules will be setup on your Windows Server, and propagated down to all machines. - Scenario 2 –
Issue: Due to new security policies within your organization, installation of software is to be prohibited by all users who are not admins.
Resolution: A group policy preventing access to certain parts of the operating system and the ability to launch non-approved executable files will prevent the installation of any software on the workstations.
- Scenario 1 –
Desktop Cloud Services
For smaller organizations who do not have the needs of an onsite Windows Server or customized desktop deployment process, utilizing cloud based services will ensure that your users are utilizing the same directories for stored files, applications, and hosted email services.
Network Design & Architecture
A proper Network Design is the backbone of your IT infrastructure. Building a powerful load balanced network is performed by certified technicians and planned for redundancy in the event disaster strikes
CCS utilizes Cisco and SonicWALL firewalls (among other leading brands) offering the highest level of security and stability for your network. With today’s web threats, the average business encounters network intrusions attempts in the thousands on a daily scale. Your firewall is the first level of defense against a network intrusion attempt, DOS attacks, network floods, malware, viruses, worms, phishing scams, keyloggers, etc…
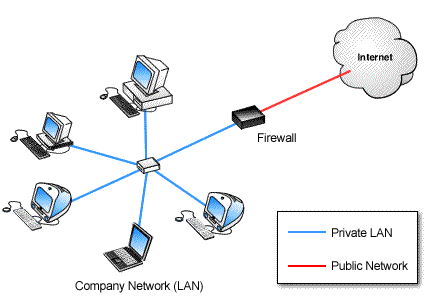
CCS will evaluate your network and recommend proper firewall protection to ensure you are protected from outside threats.
VPN/Remote Access
- Site to Site VPN
- If your business has multiple offices, why not share the resources (servers and file storage) in one office with your other locations or branches? Using site to site VPN technology, we can make this possible.
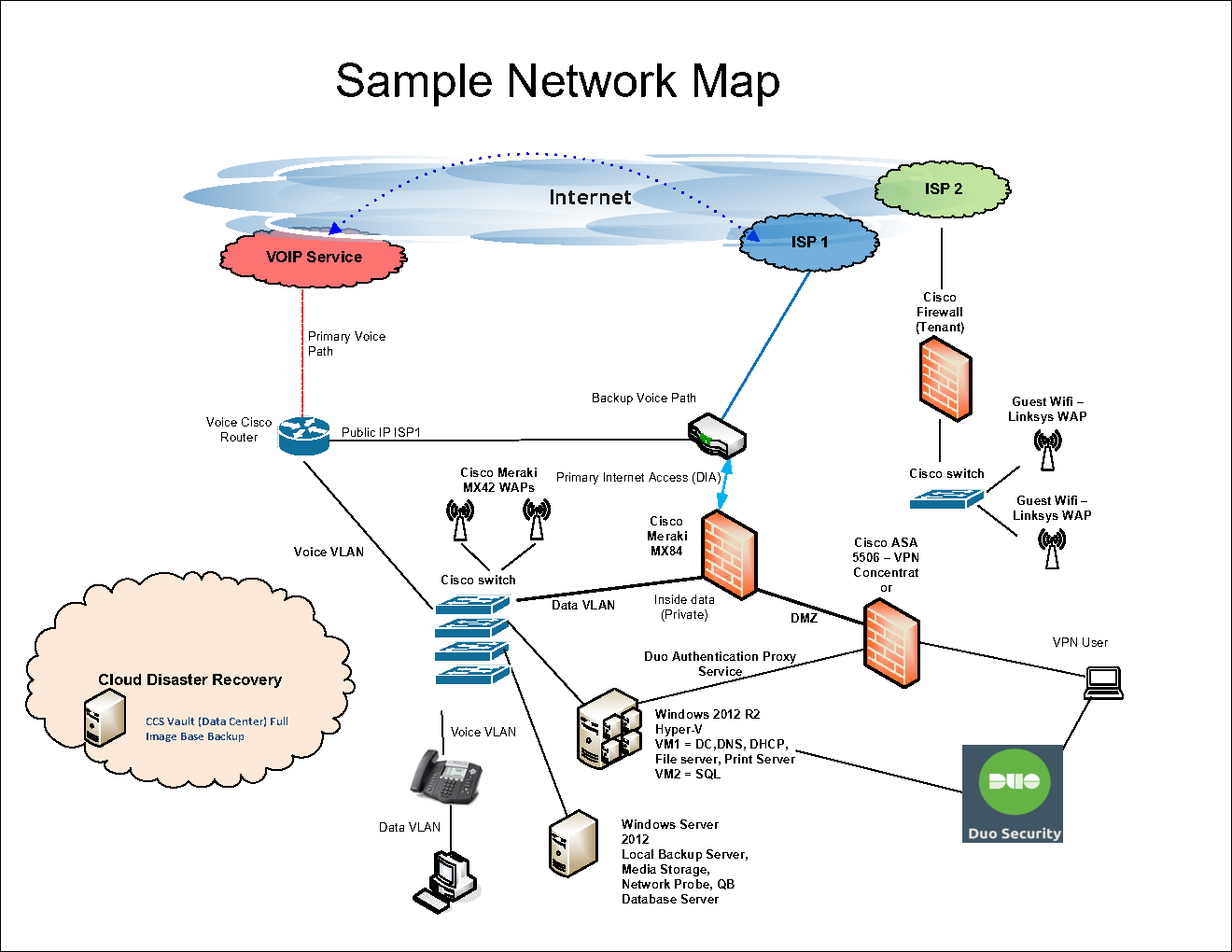
In this example, both site A and site B contain onsite servers which need to be utilized by all users of the network. Utilizing the right firewall and VPN (Virtual Private Network), both sites work together as one. The concept saves money, overhead, and IT support fees all at the same time.
Wireless Solutions
As businesses grow, usage of wireless increases. With the growth, comes a higher demand for coverage, speed, and network availability.
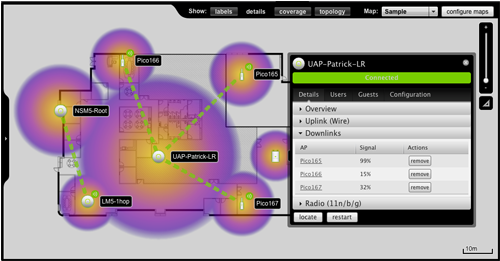
CCS has planned wireless roll-outs for small and large offices in all shapes and sizes. We start by conducting a site survey or your office, or building, and analyzing hotspots where access points can be placed. The proper placement of these access points will ensure you have coverage throughout your entire office eliminating dead zones. In addition, CCS ties your wireless infrastructure into your existing network utilizing the highest encryption levels and security across all devices.
Case Study:
The Lee Memorial Library of Allendale, NJ approached CCS with the hopes of expanding wireless coverage throughout all wings and hallways of the library across two floors. CCS engineers ran cabling through the walls from a centralized switch and strategically placed 5 managed POE (Power Over Ethernet – PoE) Access Points throughout the building ensuring 90-100% signal strength through any part of the building. In addition, private and guest networks were created to ensure security for library staff conducting internal business while providing a robust network for library patrons.
Virtualization
What is virtualization? Server virtualization is the process of running multiple servers off one physical box, thus allowing you to run multiple applications on fewer physical servers, and save money in the long haul.
As servers become more powerful, running a single server for a task creates additional overhead, additional costs, and the server itself remains underutilized. With virtualization, you can launch a new server, increase memory or processing power, and expand storage in minutes, as opposed to hours. Virtualization also makes disaster recovery more possible (details below), offering you peace of mind and greater flexibility in the event of a server crash or data center loss.
Need more reasons to Virtualize? We’ve listed a few for you!
- Energy Savings
Lower your energy bills and go Green! - Launch new servers without the need to order new equipment
Lowers setup and implementation costs - Increased uptime
With a virtualized environment you can move virtual machine from one host to another, migrate storage, and create clusters of servers with ease. - Improved Disaster Recovery
Virtual machines can be backed up as a whole. These image backups can be reverted and placed back into your production environment in the event of a disaster, avoiding days or even weeks of down time. - Separating tasks
Some server applications prefer to run on their own box. In addition, certain software vendors will not support an application if it shares a server with a conflicting program. Virtualization allows you to isolate applications to their own server, and simplifying maintenance. - Extending the life of older applications
Legacy applications which require older operating systems for maximum functionality can be preserved by launching a virtual machine hosting an older environment running your legacy programs. This allows you to save licensing costs and skip a generation of future software releases if you so choose.
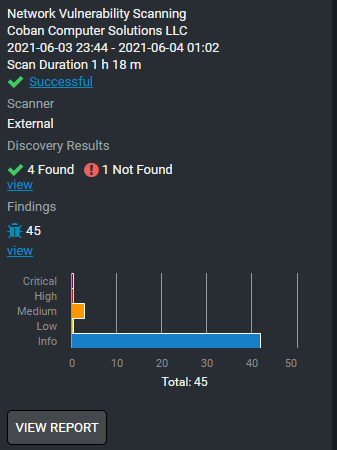
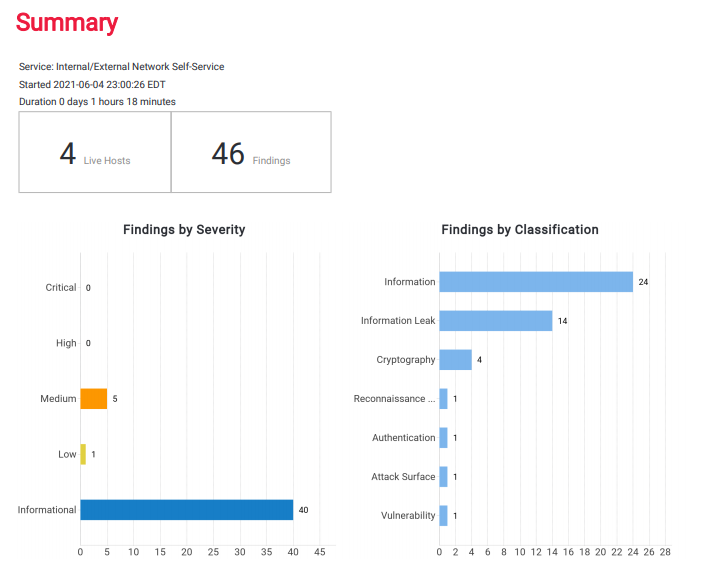
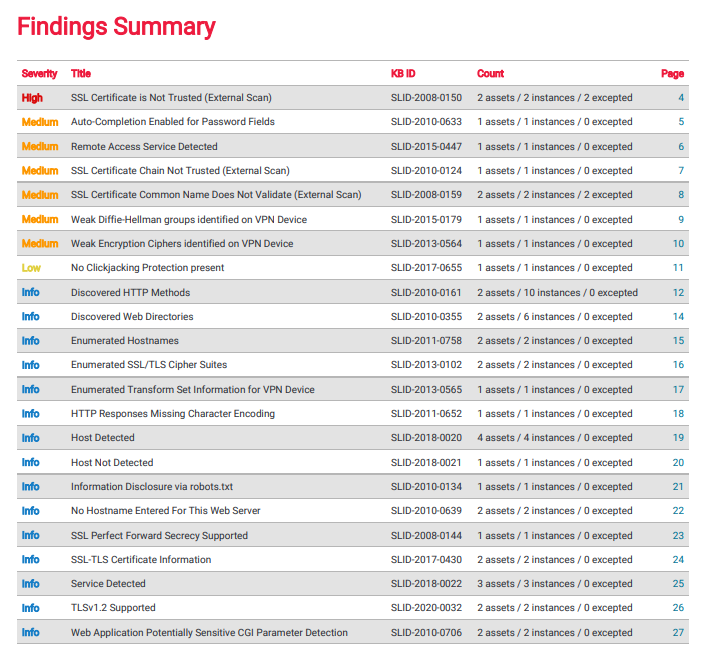
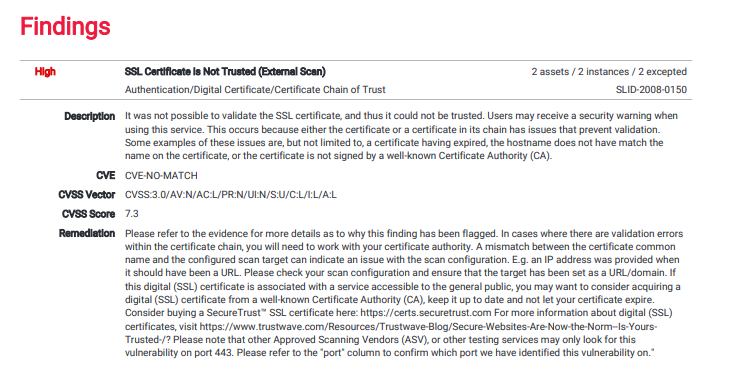
Vulnerability Scanning
Vulnerability Scanning is critical in assessing for and identifying weaknesses in your network, workstations, servers, and applications.
Dozens of new Cybersecurity threats are introduced daily on a global basis. We scan your network, look for those holes and weaknesses, and remediate them as soon as possible to prevent not only a breach of sensitive information but a loss of productivity and network downtime. An attacker relies on these vulnerabilities to exploit your network, so our goal is to be one step ahead at all times.
Cybersecurity scanning satisfies various regulatory and compliance requirements, including those affected by FISMA, USGCB, SCADA, HIPAA, PHI, HITECH, PCI DSS, FISMA, SEC, USGCB, NIST, and institutions within Education.
CCS has partnered with leading Cybersecurity firms Drawbridge and Trustwave to not only provide Vulnerability Scanning options but additional services such as:
Vendor Due Diligence
Risk Assessment Services
Penetration Testing
Phishing Exercises and Training